As the business world becomes increasingly digital, effective IT risk management is essential for organizations of all sizes. The 3 Lines of Defense model is a widely used and highly respected approach to managing risk, which can be applied to various domains, including IT. In this article, we will explore the 3 Lines of Defense model within the IT risk domain, discuss its importance for enterprises, and provide insights on how organizations can implement this strategy in their risk management efforts.
The 3 Lines of Defense Model and Its Application in the IT Risk Domain
The 3 Lines of Defense model is a risk management framework that divides organizational risk management responsibilities into three distinct layers, or “lines,” each with its own set of responsibilities and objectives as listed in figure 1 below.
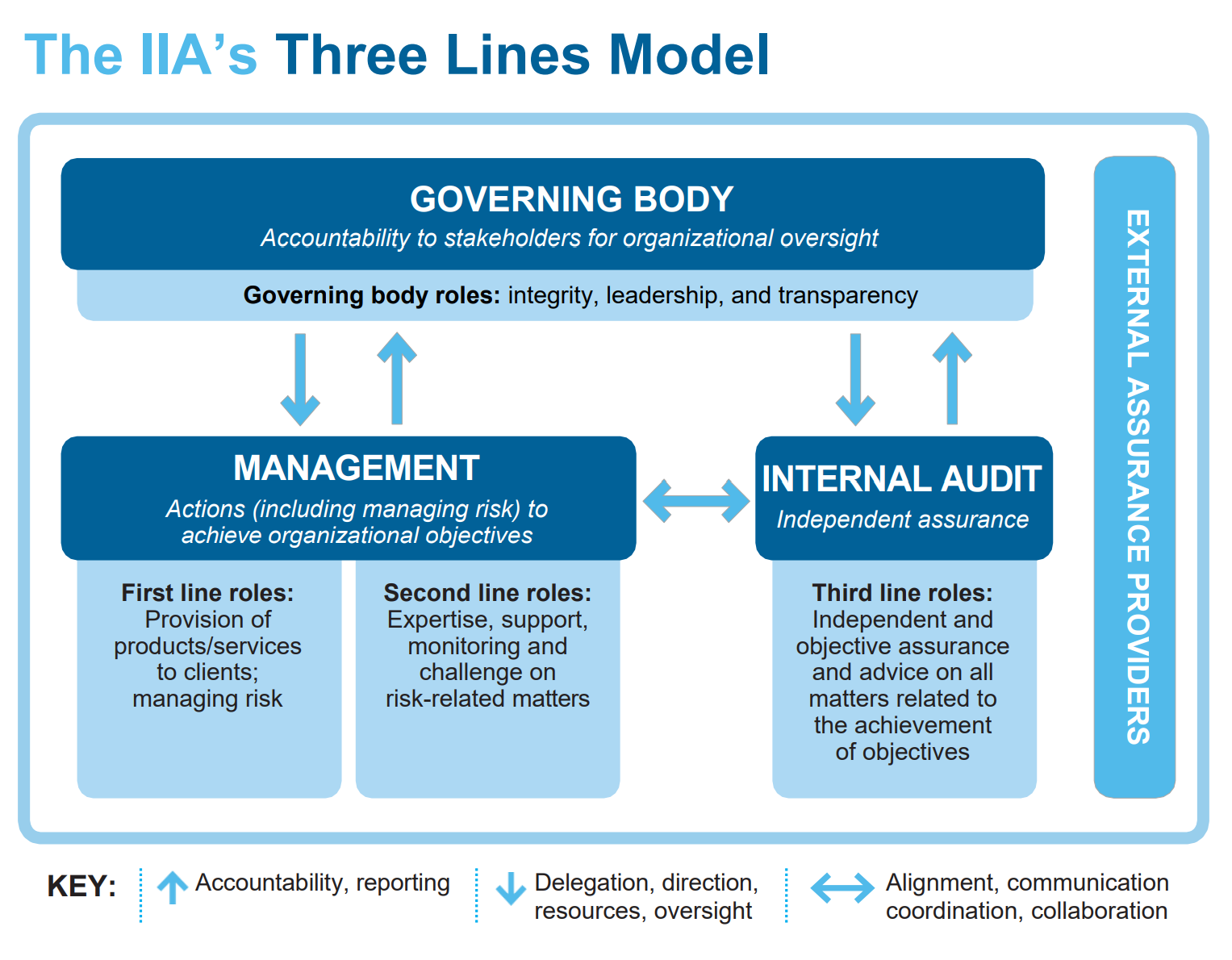
Source: Three Lines of Defense model from IIA 2020
First Line of Defense: Operational Management
In the IT risk domain, the first line of defense consists of IT operations and development teams. They are responsible for identifying, assessing, and managing IT risks, such as data breaches, system outages, and unauthorized access, on a day-to-day basis. They implement security measures, such as firewalls, encryption, and access controls, to mitigate these risks.
Second Line of Defense: Risk Management and Compliance Functions
The second line of defense includes IT risk management and compliance teams that provide oversight and support to the first line. They help to develop IT risk management policies, monitor the effectiveness of controls, and ensure that the organization adheres to relevant IT laws, regulations, and industry standards, such as the General Data Protection Regulation (GDPR) and the Network and Information Security 2 Directive (NIS2 Directive).
Third Line of Defense: Internal Audit
The third line of defense is the internal audit function, which provides an independent, objective assessment of the organization’s IT risk management, control, and governance processes. IT auditors evaluate the effectiveness of the first and second lines of defense and report their findings to senior management and the board of directors.
Importance of the 3 Lines of Defense Model for Enterprises
The 3 Lines of Defense model is essential for enterprises for several reasons:
Enterprise Risk Management
The 3 Lines of Defense model is a key component of enterprise risk management (ERM), which connects various risk domains, including IT, finance, legal, and operational risks, by providing a holistic approach to risk oversight at the enterprise level. This ensures that risk management efforts across different domains are coordinated, systematic, and comprehensive.
Regulatory Compliance
While the 3 Lines of Defense model is not explicitly mandated by specific laws or regulations, it is a widely accepted best practice and is often implicitly required or highly recommended by various regulatory frameworks. Examples of these regulations are Solvency II, GDPR, NIS2 and MiFID II.
The “Three Lines of Defense” model is most common in sectors with high levels of regulation, such as financial services, healthcare, and energy.
Implementing the 3 Lines of Defense Model
Step by step implementing the three Lines of Defense
- Assess the current risk management framework: Begin by reviewing the existing risk management practices and structure within the organization. Identify any gaps or weaknesses in the current framework and determine the areas that need improvement.
- Establish clear roles and responsibilities: Clearly define the roles and responsibilities for each line of defense. This may involve updating job descriptions, creating new roles, or clarifying existing responsibilities. An example could be:
First Line of Defense – Operational Management:
- Implement risk management processes and controls in daily operations.
- Identify, assess, and manage risks within their area of responsibility.
- Report and escalate risks as appropriate.
Second Line of Defense – Risk Management and Compliance:
- Develop and maintain risk management policies, procedures, and methodologies.
- Provide guidance and support to the first line of defense in managing risks.
- Monitor and report on the effectiveness of risk management practices.
- Ensure compliance with relevant laws, regulations, and industry standards.
Third Line of Defense – Internal Audit:
- Independently assess the effectiveness of the organization’s risk management framework.
- Evaluate the adequacy of internal controls and risk management practices.
- Provide assurance to senior management and the board of directors on the effectiveness of the risk management framework.
- Develop and implement risk management policies and procedures: Collaborate with stakeholders from all three lines of defense to develop comprehensive risk management policies and procedures. These should cover risk identification, assessment, monitoring, and reporting processes.
- Provide training and communication: Educate employees across the organization about the Three Lines of Defense model and its implementation. Provide training on risk management processes, tools, and techniques for employees in all three lines of defense. Regularly communicate the importance of risk management and the roles of each line of defense.
- Establish monitoring and reporting processes: Develop processes for monitoring the effectiveness of the Three Lines of Defense model, including key risk indicators (KRIs) and key performance indicators (KPIs). Regularly report the results to senior management and the board of directors.
- Foster a risk-aware culture: Encourage open communication and collaboration between the three lines of defense. Promote a culture where employees feel comfortable raising concerns and challenging assumptions about risk management.
- Continuously improve the risk management framework: Regularly review the effectiveness of the Three Lines of Defense model and make improvements as needed. Stay current with industry best practices, regulatory changes, and emerging risks.
- Engage external assurance providers: As appropriate, engage external assurance providers such as external auditors or specialized consultants to review and provide assurance on the effectiveness of the organization’s risk management framework and the implementation of the Three Lines of Defense model.
Best practices for (Enterprise) Risk Management
hese best practices provide guidance on risk management, internal controls, and governance, which are essential components of the Three Lines of Defense model. Each of these frameworks supports the implementation of the model in the following ways:
- Committee of Sponsoring Organizations of the Treadway Commission (COSO) Internal Control – Integrated Framework:
The COSO framework is a comprehensive guide for designing and implementing effective internal controls. It consists of five components: control environment, risk assessment, control activities, information and communication, and monitoring activities. These components align with the Three Lines of Defense model by:
- Establishing a strong control environment that supports the roles and responsibilities of each line of defense.
- Providing guidance on risk assessment processes, which are essential for the first and second lines of defense.
- Defining control activities that should be in place for managing risks, which are implemented by the first line of defense and monitored by the second and third lines of defense.
- Emphasizing the importance of information and communication between the three lines of defense.
- Offering guidance on monitoring activities to ensure the effectiveness of internal controls and the overall risk management framework, which is a key responsibility of the third line of defense.
- International Organization for Standardization (ISO) 31000, Risk Management – Guidelines:
ISO 31000 provides a set of principles, framework, and process for effective risk management. It can be applied to any organization, regardless of size, industry, or sector. The guidelines support the implementation of the Three Lines of Defense model by:
- Providing a systematic approach to risk management that can be integrated into the organization’s operations and decision-making processes.
- Emphasizing the importance of leadership and commitment from top management in establishing a risk-aware culture, which supports the functioning of the Three Lines of Defense model.
- Offering guidance on risk identification, assessment, treatment, monitoring, and reporting, which are essential activities for the first and second lines of defense.
- Encouraging the continuous improvement of risk management practices, which aligns with the goals of the third line of defense.
Conclusion
The 3 Lines of Defense model is a valuable tool for IT risk management and can be seamlessly integrated with enterprise risk management strategies. By implementing the model in the IT risk domain and incorporating it into a broader ERM framework, organizations can effectively manage risks across all areas of their operations. Adherence to relevant laws, regulations, and internationally recognized standards further strengthens the effectiveness of the 3 Lines of Defense model. Ensuring the independence of each line of defense and fostering a culture of constructive challenge among the various levels helps maintain the robustness and integrity of the risk management process. By embracing the 3 Lines of Defense model, organizations can navigate the complex and rapidly evolving digital landscape with confidence and resilience.